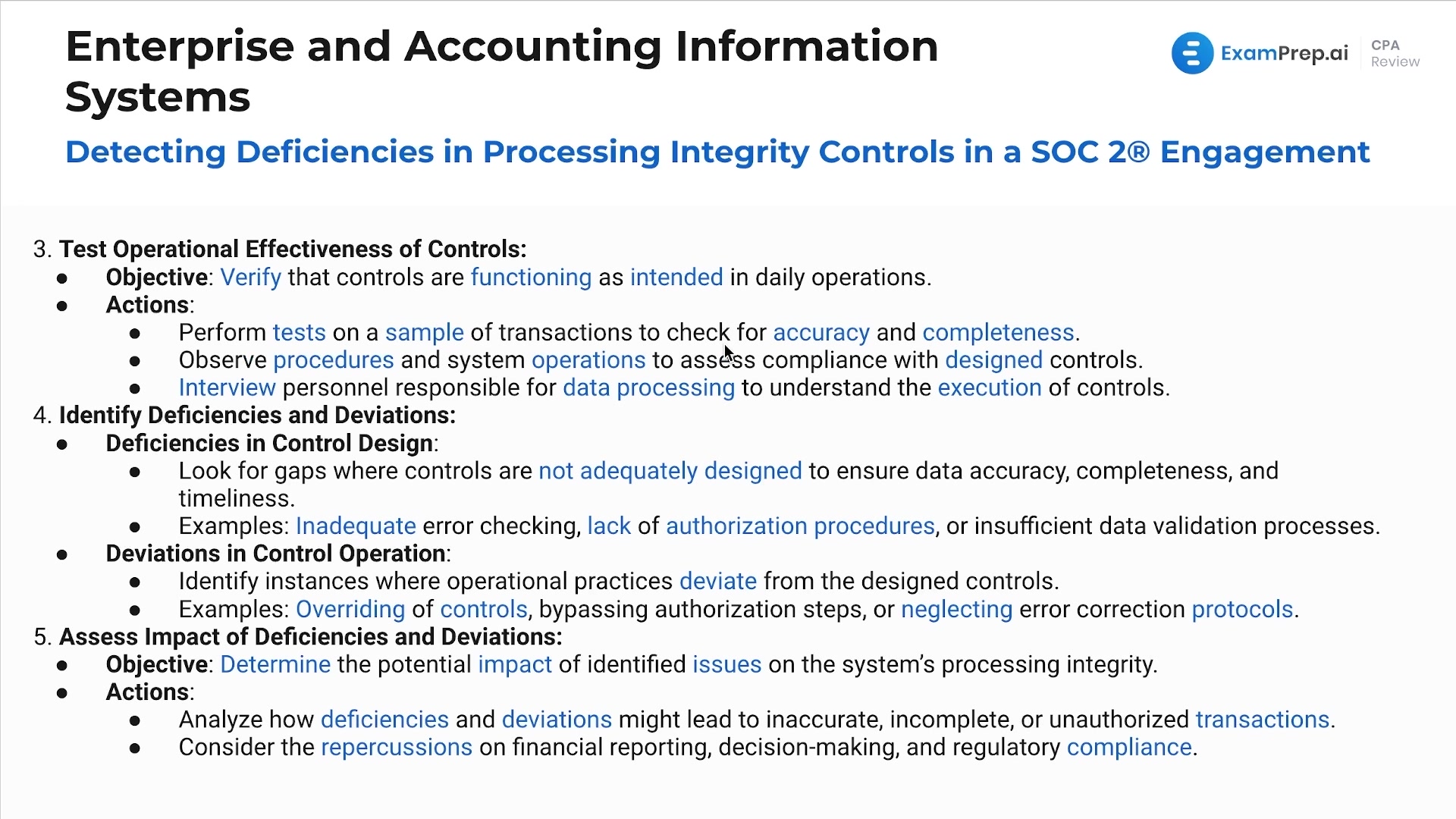
In this lesson, Nick Palazzolo, CPA, delves into the nuances of detecting deficiencies in processing integrity controls during a SOC 2 engagement. He starts by simplifying the array of SOC engagements and emphasizes their importance in assessing the processing integrity of information systems, ensuring data is delivered accurately, timely, and properly. Nick outlines a structured approach to review and evaluate control designs and their operational effectiveness, focusing on input, processing, and output controls. He also discusses how to identify and address deficiencies and deviations in system authorizations, data validation, and error correction procedures. Through practical examples and a step-by-step walkthrough, Nick provides clear insights into improving control designs and operational effectiveness, ultimately enhancing decision-making and regulatory compliance in organizational settings.
Unlock the rest of the videos in this topic free by studying on our platform! Permanently unlock up to five topics by watching videos, practicing questions, doing flashcards, or practicing simulations.
Unlock Video Free